ZigBee uses the 802.15.4 standard as the basis for its peer-to-peer communication. This standard was developed and managed by the ZigBee Alliance. The ZigBee Alliance is a consortium that invests in this standard and promotes it in the wireless arena and is increasingly concerned by the industry. However, ZigBee has its own unique application features that users should fully understand rather than rush to apply to all low-power wireless applications.
ZigBee is most commonly used as an asynchronous communication standard with CSMA/CA channel access and all the features described in the 802.15.4 chapter. For the same market segment, ZigBee offers many advantages for developers seeking quasi-guaranteed information delivery, large-scale easy network integration, and inter-device interoperability, while providing many 802.15.4 standards that cannot be directly addressed. A solution to higher level network problems.
There are three topologies for implementing a ZigBee network, as shown in Figure 3. Similar to 802.15.4, ZigBee supports peer-to-peer communication and star configuration. ZigBee adds routing protocols and hierarchical network addressing schemes over the 802.15.4 specification to implement cluster tree topologies (with the same PAN ID) and multi-hop mesh network topologies.
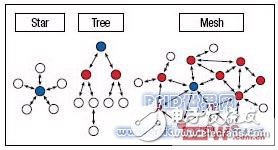
Figure 1: ZigBee network configuration
These topologies are supported by 802.15.4 FFD and RFD nodes that implement one of three logical abstraction functions. The ZigBee Coordinator, which must be FFD, will initiate network and manage network connections and most network parameters such as security keys, which are an integral part of routing messages. The ZigBee router must also be an FFD, which is responsible for forwarding messages to and from other network nodes, and implementing the mesh network characteristics of the ZigBee network while extending the overall coverage of the network. ZigBee coordinators and routers are typically powered by the mains because they should be able to receive and transmit messages at any time. If the data transmission of the application is expected to be periodic, ZigBee can also use the TDMA message transmission protocol of the 802.15.4 synchronization network. ZigBee terminal devices are implemented in RFD mode to minimize their duty cycle and resource requirements for battery-powered and long-term operation. The LBee series Zigbee wireless module launched by Shenzhen Wireless Dragon makes the Zigbee application simple.
ZigBee is ideal for applications with the following requirements:
â— Adopt standardized physical layer and lower layer protocols (IEEE 802.15.4);
â— Standardized higher layer protocols (such as mesh topology, multi-hop, etc.);
â— Full interoperability, even at the application level (public profile);
â— Low design and development requirements (application only);
â— There is intense competition between technical support and maintenance vendors/suppliers.
ZigBee accepts the following disadvantages:
â— ZigBeel Alliance member fees;
â— Certification fee (this fee is not required if it is not specifically for ZigBee or ZigBee certified products);
â— The amount of code (functional overhead can be too large to use);
â— Radio channel restrictions (limited to the channel specified in IEEEl 802.15.4).
The items listed above indicate that further clarification is required for many projects, so the standardized higher-level agreements are first described. Compared with 802.15.4, as shown in Figure 4, ZigBee can be implemented up to the transport layer of the OSI wireless application network model, and even to some session layers.
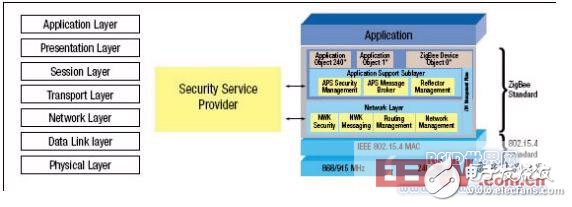
Figure 2: ZigBee's OSI network model.
The three most prominent new features of the 802.15.4 protocol are the mesh routing algorithm, a powerful security implementation, and application-level abstraction to enable a strong association between devices and interoperable "application profiles" in the target market domain. Sex.
The mesh routing algorithm of the ZigBee network makes it an extremely reliable way to deliver data between terminal devices on the network. In addition to the optional end-to-end acknowledgment that ensures packet delivery in the network, ZigBee also defines a route discovery algorithm that can communicate around the failed node, also known as ZigBee's communication self-healing capability. Route discovery is a shortest path algorithm that can be initiated by any router device and always executed for a specific destination. The principle of the calculation is that each node keeps a "link cost" record to all neighboring devices, where the link cost is the signal strength of the received signal. Accumulating the cost of the link along all routes to route, you can get the "routing cost" and calculate the routing cost of each route in the network.
A node may request route discovery by broadcasting a Route Request (RREQ) packet for a particular destination to its neighbors. Whenever a node receives an RREQ, it accumulates its link cost to the routing cost and then broadcasts the RREQ accordingly. This will be repeated until all RREQs arrive at the destination device. The destination device will then select the RREQ packet with the lowest routing cost and broadcast a Route Reply. When the RREP packet is returned to the source, all intermediate nodes will update their routing table, indicating the route to the destination. In this way, the node can lose the connection to the next hop and send a route error (RERR) packet to the network so that the next time someone tries to send a message to it, a new route discovery is initiated.
ZigBee implements a wide range of security measures. ZigBee uses three security keys, a master key for long-term security, a network key to join the network, and an encryption key for peer-to-peer communication. Encryption is performed using the AES-128 bit encryption standard. ZigBee uses MIC-128, the message integrity code, to verify the integrity of the message. In addition, by using the coordinator as a trust center to manage all security from a single node, the network can also periodically update the symmetric encryption key to achieve unlimited management of secure communications.
However, application-level abstraction may be the most competitive feature of ZigBee. Each node can be assembled to accommodate up to 270 "endpoints" or applications. For example, each endpoint can represent a light switch or a light bulb (bulb 01, bulb 02, etc.). Each endpoint can accept any type of data or send any type of data. Input data output from one endpoint to another has a single descriptor, commonly referred to as a cluster. To continue using the light bulb as an example, assume that the light bulb switch state named "light_status_on_off" is one of these data descriptors called clusters. Each endpoint can then be described based on the endpoint ID (1-270) and its cluster list (the type of data received or transmitted). In the case of cluster matching, logical binding of one-to-one or one-to-many endpoints is possible. In this example, a light bulb switch can be logically bound to any or all of the light bulbs described as supporting a "light_status_on_off" cluster. This application-level one-to-one or one-to-many binding is a powerful feature of the ZigBee protocol.
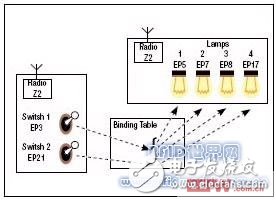
Figure 3: ZigBee's binding table can be used to control changes on the fly.
If the ZigBee Alliance defined the cluster list and the way to interpret the cluster flow between endpoints at that time, you could specify criteria for specific applications (such as light switches/light bulbs, etc.) without worrying about the specific hardware used to implement the application. The ZigBee Alliance has just completed this task, calling these standards application profiles, which not only enables applications from different vendors to fully interoperate, but also strengthens the overall competition in the ZigBee low-power wireless network target market. Sex.
If interoperability is not the primary intent of the designer, the ZigBee Alliance also allows designers to define enterprise-specific application profiles that are not shared. For the sake of brevity, we will not discuss in detail the other features of ZigBee implementation, including group addressing, frequency agility, automatic rejoin of session failures, and protocols provided by the latest version of ZigBee 2007 (also known as ZigBee PRO). Series of additional features. ZigBee PRO is still largely in the ZigBee standard category, but features added to optimize support for very large network integrations during editing.
Disadvantages of product design using the ZigBee protocol include the costs associated with developing ZigBee products: the annual membership fee paid to the ZigBee Alliance, the cost of the certified product to ZigBee, and the memory footprint of the protocol itself. The ZigBee protocol loading features are difficult to exploit in every application, requiring additional memory resources to be designed in the case of custom solutions. In some cases, the memory and resource requirements can even be limited to the final application level. As a result, some companies have introduced a radio broadcast component with an integrated MCU that preloads the ZigBee software stack, and its operation is controlled by a small number of API calls to another application-centric MCU. By using SPI communication to update the configuration of the ZigBee chip, the application MCU can be free from protocol-to-memory and resource requirements and can effectively handle other application tasks.
Home safety networkThe second and third examples will show that a slight change in requirements will result in the selection of a different protocol. This system is a home safety network installed in a renovated home environment, so rewiring will cost too much. We can choose to install several different sensors, such as smoke sensors, glass breakage sensors, motion sensors, and access control access control. Each sensor communicates with the base station, which in turn communicates with the home security monitoring company. The system should be able to interoperate with other sensors. For example, a smoke detector purchased from one company can be used with a motion detector produced by another company. The network must be highly secure against eavesdropping or tampering. Design schedules allow engineers to have a certain amount of learning time to speed up the design of network protocols. The Zigbee wireless sensor network development platform launched by Shenzhen Wireless Dragon is suitable for the second development and application of the majority of design developers.
â— Application considerations:
â— Family safety network;
â— Smoke detection, glass breakage, motion detection and occupancy detection;
â— The base station must transmit data to the home security monitoring company;
â— The user interface must be intuitive and easy to understand;
â— Need to follow industry standards;
â— Should be able to benefit from interoperability between different vendors' technologies and their associated support;
â— Robustness and reliability;
â— Key design criteria;
â— The system must be highly secure to prevent tampering and eavesdropping;
â— ease of use;
â— Standardized implementations are required to achieve reliability and security***;
â— Plan to integrate home security applications in the overall home automation network;
â— Willing to spend time learning and making full use of more complex APIs;
â— Hardware and RF considerations;
â— Most network devices are battery powered.
The final result in this example should be ZigBee, as it requires interoperability with devices from different vendors and ensures that standardized reliability and safety requirements are met.
Breaker Mcb,Mcb Circuit Breaker,32A Circuit Breaker,Miniature Circuit Breaker
ZHEJIANG QIANNA ELECTRIC CO.,LTD , https://www.traner-elec.com
