May 25th Cisco and Symantec Corporation issued security warnings on May 23, 2018, United States time: hackers used a complex, scaled malware VPNFilter to infect 500,000 routers in 54 countries around the world. A large number of router device manufacturers such as Linksys, MikroTik, Netgear, and TP-Link have been affected.

VPNFilter is powerful and can destroy firmware devices
The malware VPNFilter is considered to be the second IoT malware that supports the startup of the persistent function. In addition, the software can also scan the SCADA component to collect valuable information and support the function of deleting/destroying the firmware. , causing the affected equipment to be unavailable.
Global 500,000 routers become "broilers"
Cisco claims to have discovered VPNFilter malware on more than 500,000 routers. In 54 countries around the world, multiple brands of routers have been infected. Cisco said that the attackers did not use 0Day vulnerabilities to build the botnet, but instead used old publicly known vulnerabilities to infect routers. Symantec listed the infected device model:
Linksys E1200
Linksys E2500
Linksys WRVS4400N
Mikrotik RouterOS for Cloud Core Routers: Versions 1016, 1036, and 1072
Netgear DGN2200
Netgear R6400
Netgear R7000
Netgear R8000
Netgear WNR1000
Netgear WNR2000
QNAP TS251
QNAP TS439 Pro
Other QNAP NAS devices running QTS software
TP-Link R600VPN
Netgear, Linksys and other companies recommend that users ensure that routing products have been upgraded to the latest firmware version to protect against this network attack.
Ukraine or another cyber attack
Cisco said that the code for the VPNFilter malware overlaps with BlackEnergy, the malware that undermined Ukrainian power grids in 2015 and 2016. The malware is either related to Russian hacker groups and may launch a major hacker attack against Ukraine in the near future.
Many countries have accused Russia of being behind the scenes of the NotPetya ransomware attack. In addition, some people think that "Bad Rabbit" ransomware also comes from Russia. Their main target is Ukraine.
Foreign media reported that Russian hackers may or may plan to launch a cyber attack on Ukraine again, this time may use a botnet formed by a large number of routers.
Recently surged in infected devices
A botnet made up of malware-infected VPNFilter devices can be traced back to 2016, but researchers say that the network botnet has only begun scanning devices in recent months, and the scale has rapidly expanded in the short term. Cisco said that the botnet's operators have been focusing on infecting Ukrainian routers and IoT devices for the past few weeks, and even created special command and control servers (C&C servers) to manage these Ukrainian "broilers."
It is not yet clear what the attacker intended. As the botnet's operations accelerate, an attack will soon occur. However, Cisco is concerned that its most likely target is the Ukrainian upcoming major event.
Or aim at Ukrainian events
The UEFA UEFA Champions League final will kick off in Kiev, Ukraine, on May 26, 2018.
The Ukrainian Constitution Day (June 28) may also be the time of the attack, and this time in 2017 is the launch date of the Not Petya attack.

Three steps of malware attack
The first stage: Infect the device by the most lightweight malicious program and get boot persistence. A few weeks ago, Romanian security experts disclosed the first "hide and seek" (HNS) of the IoT malware that survived the restart of the device. A report released by Symantec states that users can perform so-called "hard resets" (that is, restore factory settings) to remove first-stage malware.
The second stage: Although the VPNFilter's malware module cannot survive the device restart, it can rely on the first stage module to download the module again when the user restarts the device. The main role of the second stage is to support the plug-in architecture of the third stage.
According to Cisco, the third stage of plug-in functionality has been discovered so far, including:
Sniff network packets and intercept traffic;
Monitor the presence of the Modubus SCADA protocol;
Communicate with the C&C server through Tor's anonymous network.
Cisco suspects that the VPNFilter manipulator has created other modules but it is not currently deployed.
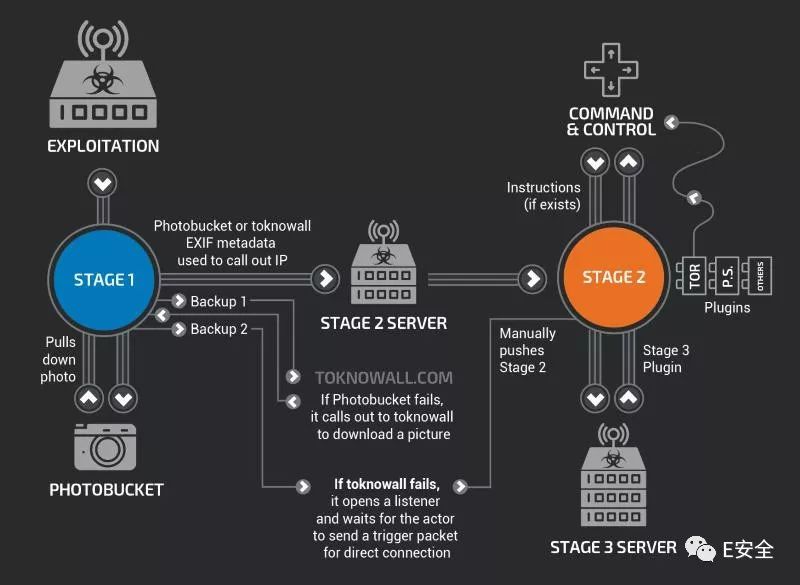
VPNFilter is an eraser
Although the VPNFilter Phase 2 module does not have boot persistence, the module at this stage is the most dangerous because it contains a self-destruction function that overwrites critical parts of the device firmware and restarts the device, resulting in the device being unavailable because the boot device The required code has been replaced with garbled code.
Cisco researchers pointed out in the report that most victims cannot recover this operation and it requires the victim to have the technical skills, knowledge or tools that the average consumer does not normally possess.
The main purpose of VPNFilter
From the current point of view, an attacker may use VPNFilter to perform the following actions:
Monitor network traffic and intercept sensitive network credentials;
Monitor the flow of traffic to SCADA equipment and deploy malicious software specifically targeted at industrial control system infrastructure;
Use this botnet's "broiler" to hide the source of other malicious attacks;
Make the router paralyzed, resulting in the Ukrainian most of the Internet infrastructure is not available.
Cisco said it is currently working with public and private entities to identify devices infected by VPNFilter and eliminate it before launching the attack. The Ukrainian Secret Service has issued security warnings.
FBI has controlled VPNFilter Botnet an important server
On May 23, 2018, the U.S. government stated that it will seek to rescue hundreds of thousands of infected routes and storage devices that were hacked and controlled.
The Federal Bureau of Investigation (FBI) agent holding a court order has taken control of an important server in the botnet, discovered the victim of the botnet, and severely thwarted the botnet's ability to re-infect the target. According to TheDailyBeast, VPNFilter is related to the Russian hacking organization Fancy Bear (aka APT28).

Court records show that the FBI has been investigating the VPNFilter botnet since August 2017 when FBI agents learned about a victim in Pittsburgh, USA (home router was infected). The victim voluntarily gave the router to the FBI agent and also allowed the FBI to use the network tap on its home network to observe network traffic.
The device can get out of control after restart
The FBI used the material provided by the victims to identify a key weakness of this malware: if the victim restarts the infected router, the malicious plug-in will disappear and only the core code of this malware will survive. The core code is reprogrammed to connect to a hacker deployed C&C server over the Internet. The core code first checks the specific images that are hosted on the Photobucket (hot picture website) site and hide information in the metadata. If the core code cannot find these pictures (in fact it has been deleted from Photobucket), it will go to the emergency backup control point of the hard-coded website ToKnowAll[.]com.
On May 22nd, the FBI agent in Pittsburgh asked the federal judge in the area to issue an order to allow the domain name registration company Verisign to hand over the ToKnowAll[.]com address to the FBI to further investigate, disrupt the botnet-related criminal activities, and assist Remedial work. The judge agreed to the FBI's request and the FBI took over the domain on May 23.
Vikram Thakur, Symantec’s technical director, said that this move can effectively stifle the ability of this malicious software to resume activities after it restarts. The VPNFilter malware Payload itself is not persistent, so it cannot survive after the router is restarted. Ordinary consumers can restart the router to prevent such network attacks.
The FBI is collecting the internet IP address of the infected router (which communicates to ToKnowAll[.]com) and the FBI can use IP information to clean up the botnet's infection.
Thakur noted that the FBI can track victims of infections and provide such information to local Internet service providers. Some Internet service providers have the ability to remotely restart the router. Other such providers can notify users and urge them to restart the device. He said that from a technical perspective, VPNFilter will not send victims' browsing history or other sensitive data to the FBI. Its threat capabilities simply require an additional Payload. The infected router is not currently leaking data to ToKnowAll[.]com.
Immersion Cooling is a technique used to cool components of IT equipment that consists of submerging the computer components in a thermally conductive and dielectric liquid. Through this practice, the servers are cooled and heat is transferred from the source to the liquid.
When we talk about Immersion Cooling, we also need to discuss the different types of Immersion Cooling, as well as the applications of Immersion cooling. The practice of Immersion Cooling has a multitude of benefits particularly as it allows datacenters to be managed in a greener and more sustainable manner. Environmental concerns has been a huge catalyst for the adoption of the technology in recent years.
deionized water
mineral oil
fluorocarbon-based fluids
synthetic
Immersion Cooling systems used to have a higher fluid cost than water cooling, but this is already changing.
A wide variety of liquids exist for this purpose, the most suitable being transformer oils and other electrical cooling oils. Non-purpose oils, including cooking, motor and silicone oils, have been successfully used for cooling personal computers
water cooling,oil cooling,immersion cooling box,liquid immersion cooling,apw12 power supply
Shenzhen YLHM Technology Co., Ltd. , https://www.hkcryptominer.com
