As more and more devices need to communicate or control through the Internet, interconnection and security functions become the main design requirements faced by designers in addition to operating systems
Most designers use traditional design steps when designing embedded systems: first select RTOS (real-time operating system), and then build software applications on this basis. As for other components, such as network protocols, they are selected based on their compatibility with the selected RTOS. This selection sequence is not suitable for future embedded system design.
The interconnection and mobility characteristics of embedded devices have become increasingly prominent, thereby enhancing the requirements for interconnection and security. Today, no system is designed without considering how to interconnect with other systems. From home alarm equipment, car monitoring equipment to industrial control equipment, OEMs of embedded systems provide products with more powerful performance and better usability for users through IP interconnection technology.
In the past, when choosing an operating system, people needed to carefully evaluate the advantages and disadvantages of the operating system and the available development tools. The design engineer's job is to ensure that the selected operating system is qualified for the largest scope of work and meets the needs of future engineering development.
Now, as more and more devices need to communicate or control through the Internet, interconnection and security functions have become the main design requirements faced by designers in addition to operating systems. Embedded system engineers must carefully select interconnection and security protocol stacks in the early stage of the design to ensure that the TCP / IP protocol stack and the corresponding security and mobility features can meet most functional upgrades during the life cycle of the embedded system And the need for design updates.
For example, for companies and government offices, factories, and R & D laboratories throughout the network, the more devices that communicate through the Internet (or Intranet, VPN), the more convenient and practical these devices are for users.
However, if hackers use wireless devices to conduct sabotage outside the high walls of the laboratory, how should we respond? Especially for the government and the military system, the consequences of such destruction may be irreversible.
The scale of wired and wireless networks used for communication by a large number of embedded devices is growing, and there is an urgent need for reliable interconnection and security performance guarantees. Vulnerable network security means a great risk to the front end of embedded system design.
Foundation: TCP / IP stack
Just as RTOS is traditionally the basic building block of most embedded systems, the TCP / IP stack is the foundation of network interconnection and security. The TCP / IP stack is not only responsible for communication between devices, but also the core software on which many other network interconnection and security modules depend.
The TCP / IP stack is essentially a software module with a hierarchical structure, and its function is to transmit information through the Internet. TCP / IP is a misleading statement because TCP and IP are just two of the many protocols used by the TCP / IP stack to communicate. The size of the stack can be large or small, such as mobile phones and PDAs, and large and complex stacks such as those that handle VPN communications for multinational companies.
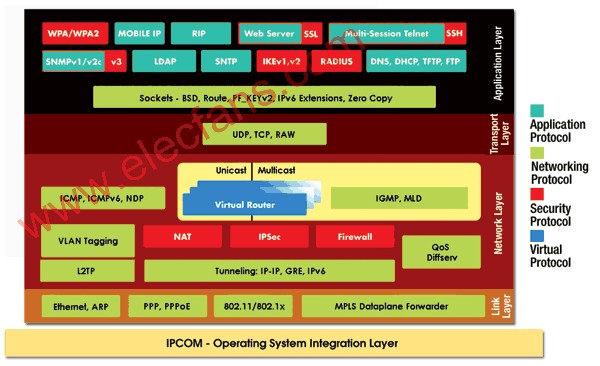
Figure 1 TCP / IP protocol stack similar to Interpeak's IPNET, in which integrated components support multiple network interconnection functions, IPv4 / IPv6, and multiple security functions
Figure 1 shows a protocol stack that integrates multiple components. The protocol stack in this example has a high degree of security, can be seamlessly moved, and supports IPv4 and the new IPv6 protocol. The network and transport layer form the core of this stack.
The network layer is responsible for message processing, and converts logical addresses and names into physical addresses, and the transport layer ensures data integrity. This layer uses two basic protocols: Transmission Control Protocol (TCP) and User Datagram Protocol (UDP). When a transmission error occurs, TCP is responsible for resubmitting the data and making the host maintain multiple connections at the same time. UDP is a datagram service. When error correction is not required, UDP can enhance network traffic at the transport layer.
Complexity: new challenges
In the past, network interconnection was a secondary factor, and many system designers usually build their own network protocol stack, or simply simplify this work. Communication between devices is usually relatively simple and limited to a small area.
But now, a large number of devices are interconnected through the Internet, and the interconnect protocol stack becomes more and more complex. Intricate interconnections and security protocols have grown exponentially, and global network standards are also rapidly developing to cope with the latest security challenges and difficulties caused by the large number of devices communicating on the Internet.
In addition to this, the major change in the Internet is the change from the current IPv4 protocol to the IPv6 protocol. IPv4 supports about 4 billion addresses, and people have come up with some ways to open up additional address space in "private" networks. IPv6 supports 3.4 × 1038 addresses, which means that it can provide 6.70 × 1017 addresses per square millimeter on the earth. With the gradual popularization of IPv6, many devices need to be able to support both IPv4 and IPv6 communications.
According to the device types and interconnection characteristics required by IPv6, from mobile IP to QoS, virtual routing, IPv6 pipes, and more and more new technologies, higher performance and standard compatibility are required. Growth and simultaneous development.
For most applications, the problem is no longer to build your own TCP / IP stack, but to choose a suitable protocol stack. We will face the challenge of using multiple RTOS. In this case, the network interconnection and security protocol stack need to be transplanted to multiple RTOS. We must be aware of the possibility of this demand early in the development of the system.
To a certain extent, the development path of embedded system design is very similar to that of PC. In the early 1980s, the main role of PCs was to deal with spreadsheets and word processing. People chose PCs based on these functions. Today, many end users need to quickly transfer data over the Internet and also need to have multimedia capabilities. Word processing and spreadsheet calculations have become ancillary functions.
Similarly, in the embedded field, we rely heavily on the performance and reliability of various RTOSs that have been in use for more than a decade. However, we must change our focus and realize that any compromise between network interconnection and security issues will damage the value of the entire embedded system. Therefore, coping with the challenges of network interconnection and security has become the primary issue to be considered in system design.
Could you share which points you care more when choose a teacher laptop? Size, cpu, storage, memory, battery, screen, fingerprint or backlight? As one of the top laptops for teachers in 2022, this 15.6 inch celeron N5095 or J4125 online teaching laptop is of the special necessary features a laptop for online teaching has. For example, high quality 1080P screen, bigger battery, updated storage and memory, mid-level cpu, etc. So many clients choose this model as laptop for teachers malaysia or laptops for teachers program.
Of course, there are other type Education Laptop, like 14 inch windows 10 64 gb Student Laptop, 15 inch 10th good laptops for university students, 16.1 inch i7 9th hq 4gb video graphic laptop, etc.
If you have other type device interest, just let us know since we also customize android or windows tablet, Mini PC and All In One PC.
Believe always have a right one meeting your special demand, no matter for student project, business tender, academic institution or reselling.
Teacher Laptop,Online Teaching Laptop,Top Laptops For Teachers,Laptop For Teachers Malaysia,Laptops For Teachers Program
Henan Shuyi Electronics Co., Ltd. , https://www.shuyihost.com
